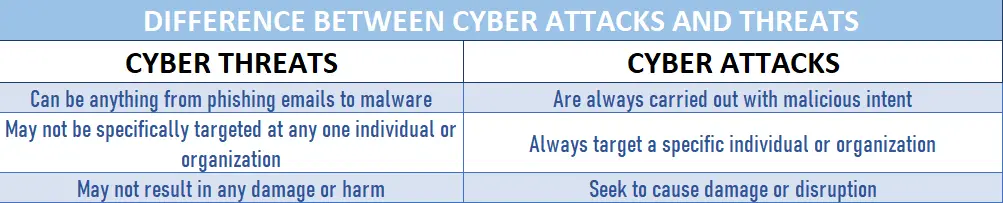
Cyber threats are defined as activities that could potentially harm or disrupt a computer system. Cyber-attacks, on the other hand, are attacks that use computers and technology to inflict damage. Both cyber threats and cyber-attacks can occur through digital means (through emails and social media posts, for example) or physical means (via break-ins into systems). In either case, they can have far-reaching consequences for individuals and organizations who fall victim to them. Understanding the difference between these two types of attacks will help you better protect yourself from online risks.
What is a cyber threat?
A cyber threat is a type of online security threat that can target individuals, businesses, or governments. Cyber threats can come in many different forms, such as viruses, phishing scams, ransomware, and spyware. While some cyber threats are relatively harmless, others can have devastating consequences.
What is a cyber-attack?
(Image by Tumisu from Pixabay )

A cyber-attack is a type of security threat that targets computer systems, networks, or personal devices. Hackers use a variety of methods to gain access to a system, such as phishing or malware. Once they have gained access, they can wreak havoc by stealing data, deleting files, or even taking control of the system. Cyber-attacks can be very damaging to both individuals and businesses, which is why it is important to be aware of the different types of attacks and how to protect yourself against them.
Cyber threats Vs Cyber-attacks – Key differences
Cyber threats are typically malicious online activity that seeks to exploit computer systems or networks. A cyber-attack is a type of cyber threat that specifically targets and seeks to damage or disrupt a system or network. In other words, all cyber-attacks are cyber threats, but not all cyber threats are cyber-attacks.
How to protect yourself from cyber-attacks
It is important to protect yourself from cyber-attacks by understanding the difference between cyber threats and cyber-attacks. Cyber threats are any type of online threat, such as viruses, phishing scams, and malware. Cyber-attacks are attempts to gain unauthorized access to your computer or network. They can also be used to disable or damage systems.
There are a few steps you can take to protect yourself from cyber-attacks:
- Use strong passwords and never reuse them.
- Enable two-factor authentication whenever possible.
- Keep your software up to date.
- Be careful about what you click on and download.
- Backup your data regularly.
What are types of cyber threats?
There are many types of cyber threats, but some of the most common include:
Malware – This is a type of software that is designed to damage or disable computers. It can be spread through email attachments, downloads, and even visits to infected websites.
Phishing – This is a type of online fraud that involves tricking people into revealing personal information or clicking on malicious links. Phishing emails often look like they’re from legitimate businesses or organizations, but they’re not.
Ransomware – This is a type of malware that puts your personal data at risk unless you pay a ransom to the attacker. Once ransomware encrypts your files, it’s very difficult (if not impossible) to decrypt them without the right key.
Botnets – This is a type of network made up of infected computers, or “bots,” that are controlled by attackers without the owner’s knowledge. Attackers use botnets for all sorts of nefarious purposes, including sending spam emails and launching denial-of-service attacks.
Spyware – This is software that secretly collects information about you without your knowledge or consent. It can track your internet usage, steal your passwords and financial information, and more.
What are types of cyber attacks?
There are many types of cyber attacks, but some of the most common include:
Denial of service (DoS) attack: A DoS attack is when a malicious actor tries to make a network or system unavailable to its users by flooding it with traffic or requests until it can no longer handle the load and crashes. This can be done by infecting devices with malware that allows the attacker to take control of them and use them to send traffic to the target, or by simply overwhelming the target with traffic from multiple sources.
Data theft: Data theft is when an attacker gains unauthorized access to data, usually by breaching a system or network and extracting it. This can be done for many reasons, such as stealing sensitive information like credit card numbers or intellectual property, or simply destroying data to disrupt operations.
Malware: Malware is short for “malicious software,” and refers to any software that is designed to harm a system or its users. This can include viruses, which spread themselves and cause damage, or ransomware, which encrypts data and demands a ransom for the decryption key.
Phishing: Phishing is a type of social engineering attack in which an attacker attempts to trick someone into giving them sensitive information, such as passwords or financial information. This is often done by sending an email that appears to be from a legitimate company or website, but contains links that lead to a fake site where the
Who is behind cyber attacks?
(Photo by Clint Patterson on Unsplash )

There is no one definitive answer to this question – cyber attacks can be carried out by individuals, groups, or even states. However, what we do know is that the motivations behind these attacks vary widely. Some attackers may be motivated by financial gain, while others may be looking to cause destruction or disrupt service. Additionally, some attackers may have political or ideological motivations.
Who is responsible for cyber attacks?
When it comes to cyber attacks, there is no one definitive answer as to who is responsible. attribution of such attacks is often difficult, and may involve a combination of human and technical factors. In some cases, state-sponsored actors are believed to be behind certain attacks, while in others, criminal gangs or individual hackers may be to blame.
In general, however, it is important to remember that anyone with the requisite skills and motivation can carry out a cyber attack – meaning that we all have a role to play in prevention and mitigation. By increasing our awareness and understanding of cybersecurity risks, we can make it harder for attackers to succeed.
Who is most at risk for cyber attacks?
There is no one definitive answer to this question as the risk factors for cyber attacks can vary depending on the type of attack and the specific target. However, some groups of people who may be more at risk for cyber attacks include:
- People who use the internet regularly and/or have a lot of personal information stored online
- Small business owners or employees, as small businesses are often targeted by hackers
- People who work in fields that deal with sensitive information, such as healthcare or finance
- Children and teenagers, as they are often less aware of the dangers of clicking on links or providing personal information online
How many cyber attacks happen per day?
The number of cyber attacks that happen every day is constantly increasing. There are many different types of attacks, and they can come from many different sources. Some attacks are targeted at specific individuals or organizations, while others are more generalized. The best way to protect yourself from cyber attacks is to stay informed and be aware of the latest threats.
Are cyber attacks serious?
Yes, cyber attacks are definitely serious. Here are some statistics that show just how big of a problem they are:
- In 2015, there were more than 4,000 ransomware attacks every day.
- In 2016, the average cost of a data breach was $4 million.
- In 2017, there were more than 1.2 billion data records stolen in breaches.
These numbers show that cyber attacks are not only becoming more common, but they’re also becoming more costly. And as our reliance on technology grows, the stakes will only get higher. So it’s important to be aware of the threat and take steps to protect yourself and your business.
How cyber attacks affect an organization?
As digital technologies become increasingly commonplace, organizations face an ever-growing number of cyber threats. A cyber attack is a type of offensive action that targets computer networks or devices. Cyber attacks can vary in their motives, scope, and sophistication. Some attacks are carried out by individuals or small groups, while others are perpetrated by nation-states or organized crime syndicates.
Cyber attacks can have a range of devastating consequences for organizations. Financial losses, reputational damage, and legal liabilities are just some of the risks faced by companies that fall victim to these kinds of attacks. In addition, cyber attacks can lead to the loss or theft of confidential data, which can give attackers an advantage in future negotiations or allow them to commit fraud or identity theft.
Organizations can take steps to protect themselves against cyber attacks, but it is important to remember that no system is 100% secure. The best defense against cyber attacks is a combination of technical measures (such as firewalls and intrusion detection systems) and non-technical measures (such as employee training and incident response plans).
When did cyber attacks begin?
It is difficult to pinpoint when cyber attacks began because it depends on how you define a cyber attack. If you consider any type of unauthorized access or activity on a computer network to be a cyber attack, then the first recorded instance of such an attack took place in the late 1960s. However, if you only consider attacks that specifically target and seek to damage or disrupt computer networks or systems, then the first recorded instance of such an attack took place in the early 1980s.
What was the most serious cyber attck?
There is no single answer to this question as the most serious cyber attack will vary depending on the context and objectives of the attacker. However, some notable examples of serious cyber attacks include:
- The Stuxnet worm which caused physical damage to Iranian nuclear centrifuges.
- The Sony Pictures hack which led to the release of sensitive information and financial losses for the company.
- The cyberattack on Ukraine’s power grid which caused widespread blackouts.
What are the biggest cyber attacks in history?
There have been many high-profile cyber attacks in recent years, but some stand out above the rest. Here are four of the biggest cyber attacks in history:
The NotPetya Attack
In June of 2017, a ransomware attack known as NotPetya hit computer systems around the world. The attack originated in Ukraine, but quickly spread to other countries, including the United States, Europe, and Russia. NotPetya caused billions of dollars in damage and disrupted operations at major companies, including Maersk and Merck.
The Sony Hack
In November of 2014, hackers breached Sony Pictures’ computer systems and stole a large amount of sensitive data. The hackers then released some of this data publicly, embarrassing Sony and causing it financial damage. The U.S. government later attributed the hack to North Korea.
The Target Breach
In December of 2013, hackers breached Target’s computer systems and stealing credit and debit card information for millions of customers. The breach caused Target significant financial damage and led to the resignation of its CEO.
The Yahoo! Data Breach
One of the largest data breaches in history occurred at Yahoo! in 2014. Hackers stole data for over 500 million user accounts, including sensitive information such as names, dates of birth, email addresses, phone numbers, and hashed passwords. This breach resulted in a decline in Yahoo!’s value and eventual sale to Verizon
What is the biggest cyber threat today?
Cyber threats are different from cyber-attacks. A cyber-attack is an attempt to carry out a harmful or destructive act by using the Internet, including through unauthorized access to systems and data. A cyber threat is a possible event or circumstance that could result in harm to systems or data if it occurred. Cyber threats can include unauthorized access, destruction, alteration, or interference with system operations.
Featured Image By – Photo by Pixabay:








