Asymmetric encryption, with its use of two keys – a public key for encrypting data and a private key for decrypting it – provides a high level of security. Symmetric encryption uses a single key for both encrypting and decrypting data. This makes it faster and more efficient than asymmetric encryption.
TL;DR Asymmetric encryption Vs. Symmetric encryption
Asymmetric encryption uses two mathematically-linked keys, a public key for encryption and a private key for decryption. It offers enhanced security, secure key exchange, and digital signatures,
Symmetric encryption uses the same key for both encryption and decryption, making it faster and more efficient than asymmetric encryption. It is ideal for bulk data encryption and resource-constrained environments.
Hybrid encryption, a combination of both methods, is often used to achieve a balance of security and efficiency in various applications.
What is Asymmetric Encryption?

Imagine a magical lock that requires not one, but two unique keys to unlock it. That’s the essence of asymmetric encryption. Also known as public-key encryption, this technique utilizes a pair of mathematically-linked keys – a public key and a private key.
The public key, as the name suggests, is available to anyone who wants to send encrypted messages. It acts as the lock for encrypting data and can be freely shared with others.
The private key is kept securely by its owner and serves as the exclusive key to decrypt messages that have been encrypted with the corresponding public key.
When someone wants to send you an encrypted message, they use your publicly available key to lock up their message in an impenetrable box. Only you possess the unique private key capable of unlocking this digital treasure chest.
Asymmetric encryption offers an ingenious solution for secure communication over open networks like the internet. With its dual-key system, it ensures confidentiality without requiring both parties involved in communication to share a common secret beforehand.
What is Symmetric Encryption?
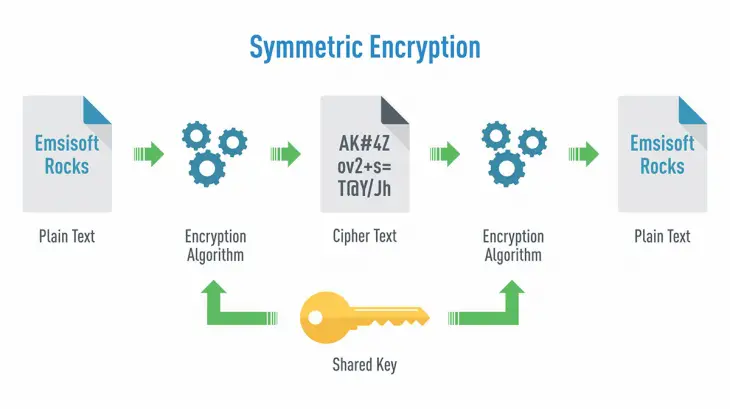
Symmetric encryption, also known as secret key encryption, is a cryptographic method that uses the same key for both encrypting and decrypting data. Here the sender and receiver use a shared secret key to scramble and unscramble messages.
When using symmetric encryption, data is divided into fixed-size blocks called plaintext. The algorithm then applies various mathematical operations on these blocks along with the secret key to transform them into ciphertext. This process ensures that only individuals possessing the correct key can decipher the encrypted information.
Asymmetric encryption Vs. Symmetric encryption – Key differences
| Aspect | Asymmetric Encryption | Symmetric Encryption |
|---|---|---|
| Key Type | Uses a pair of keys: Public key and Private key | Uses a single shared secret key |
| Key Distribution | Public keys are shared openly, Private keys are kept secret | The shared secret key must be distributed securely among parties |
| Encryption & Decryption | Different keys are used for encryption and decryption | The same key is used for both encryption and decryption |
| Security | Offers higher security due to separate key pairs | Relatively less secure as the same key is used for encryption and decryption |
| Key Generation Complexity | More computationally intensive to generate key pairs | Easier to generate a single shared secret key |
| Speed | Slower compared to symmetric encryption | Faster compared to asymmetric encryption |
| Scalability | Less scalable for encrypting/decrypting large amounts of data | More scalable for encrypting/decrypting large amounts of data |
| Applications | Used for secure key exchange, digital signatures, and identity verification | Suitable for encrypting large amounts of data between trusted parties |
| Examples | RSA, ECC, DSA | AES, DES, 3DES, Blowfish, ChaCha20 |
Asymmetric encryption and symmetric encryption each have their own advantages and use cases. Asymmetric encryption is often used for secure key exchange and digital signatures.
Symmetric encryption is more efficient for encrypting large amounts of data between parties that share the same secret key. Depending on the specific security requirements and use scenarios, one type of encryption may be more suitable than the other.
Advantages and Disadvantages of Asymmetric Encryption
Advantages of Asymmetric Encryption
- Enhanced Security: Asymmetric encryption provides a higher level of security compared to symmetric encryption.
- Secure Key Exchange: Asymmetric encryption is ideal for secure key exchange between parties. The sender can encrypt data using the recipient’s public key, and only the recipient with the corresponding private key can decrypt the data.
- Digital Signatures: Asymmetric encryption enables the creation and verification of digital signatures, which ensures the authenticity and integrity of the data.
- No Need for Secure Key Distribution: With asymmetric encryption, public keys can be openly shared, removing the need for a secure channel to distribute keys.
- Wider Range of Applications: Asymmetric encryption finds applications in various scenarios, such as secure email communication, online transactions, and digital certificates used in SSL/TLS for secure website connections.
Disadvantages of Asymmetric Encryption
- Computational Complexity: Asymmetric encryption algorithms are computationally intensive compared to symmetric encryption. Generating key pairs, encryption, and decryption processes can be slower and require more processing power, especially for large datasets.
- Key Management Overhead: Managing key pairs (public and private keys) can be challenging, particularly when dealing with a large number of users or devices.
- Performance Impact: Due to the computational complexity, asymmetric encryption may not be suitable for real-time encryption and decryption of large volumes of data, such as in high-speed network communication.
- Key Size: Asymmetric encryption requires larger key sizes compared to symmetric encryption to achieve the same level of security, which can increase the storage and transmission overhead.
- Vulnerability to Quantum Computing: Some widely used asymmetric encryption algorithms, like RSA, are vulnerable to potential future attacks by quantum computers.
Asymmetric encryption offers robust security, secure key exchange, and digital signatures. However, its computational complexity and key management overhead can impact performance, making it less suitable for certain applications that require high-speed data encryption.
A well-designed cryptographic system often combines both asymmetric and symmetric encryption to leverage their respective strengths and address their limitations effectively.
When to Use Asymmetric or Symmetric Encryption
The decision to use asymmetric or symmetric encryption depends on the specific security requirements and use cases of the application or system. Each type of encryption has its strengths and weaknesses, and they are often used together in hybrid encryption for a more robust security approach.
Here are some scenarios where each encryption type is typically used:
Asymmetric Encryption
- Secure Key Exchange: Asymmetric encryption is ideal for secure key exchange between two parties who do not already share a secret key. One party can use the recipient’s public key to encrypt the data, and only the recipient with the corresponding private key can decrypt it.
- This is commonly used in protocols like SSL/TLS for secure communication between a client and a server.
- Digital Signatures: Asymmetric encryption enables the creation and verification of digital signatures. Digital signatures are crucial for verifying the authenticity and integrity of data, ensuring it has not been tampered with during transmission.
- Identity Verification: Asymmetric encryption can be used for identity verification in systems like public key infrastructure (PKI) or certificate-based authentication.
- Secure Email Communication: Asymmetric encryption is used to encrypt email communications so that only the intended recipient can read the message.
Symmetric Encryption
- Efficiency: Symmetric encryption is much faster and more efficient than asymmetric encryption. It is suitable for encrypting large volumes of data in real-time, making it ideal for applications that require high-speed encryption and decryption.
- Bulk Data Encryption: Symmetric encryption is commonly used for bulk data encryption, such as encrypting files, databases, or data streams.
- Resource-Constrained Environments: In environments with limited computational resources, such as embedded systems and mobile devices, symmetric encryption is preferred due to its efficiency and lower overhead.
- Data Privacy in Closed Systems: In a closed system where all parties share a secret key securely, symmetric encryption can be a practical choice for maintaining data privacy among trusted participants.
Hybrid Encryption
In many real-world applications, a combination of both asymmetric and symmetric encryption is used to leverage their respective strengths while mitigating their weaknesses. This approach is known as hybrid encryption.
For example, in secure communication protocols like SSL/TLS, a combination of both encryption types is used.
The initial handshake uses asymmetric encryption to securely exchange a symmetric session key. Once the session key is established, symmetric encryption is used for fast and efficient data encryption during the session.
Use asymmetric encryption when secure key exchange or digital signatures are required. Use symmetric encryption for high-speed data encryption in resource-constrained environments or when all parties share a secure key.
For many applications, a hybrid encryption approach combining both encryption types provides an effective and well-rounded security solution.
Image Credits
Featured Image By – Kiroe from Pixabay
Image 1 By – Nicobon, CC BY-SA 4.0, via Wikimedia Commons
Image 2 By – Munkhzaya Ganbold, CC BY-SA 4.0, via Wikimedia Commons