Network topology deals with physical connectivity and spatial arrangements, while network architecture encompasses higher-level considerations such as communication protocols, security measures, and performance optimization.
What is network topology?
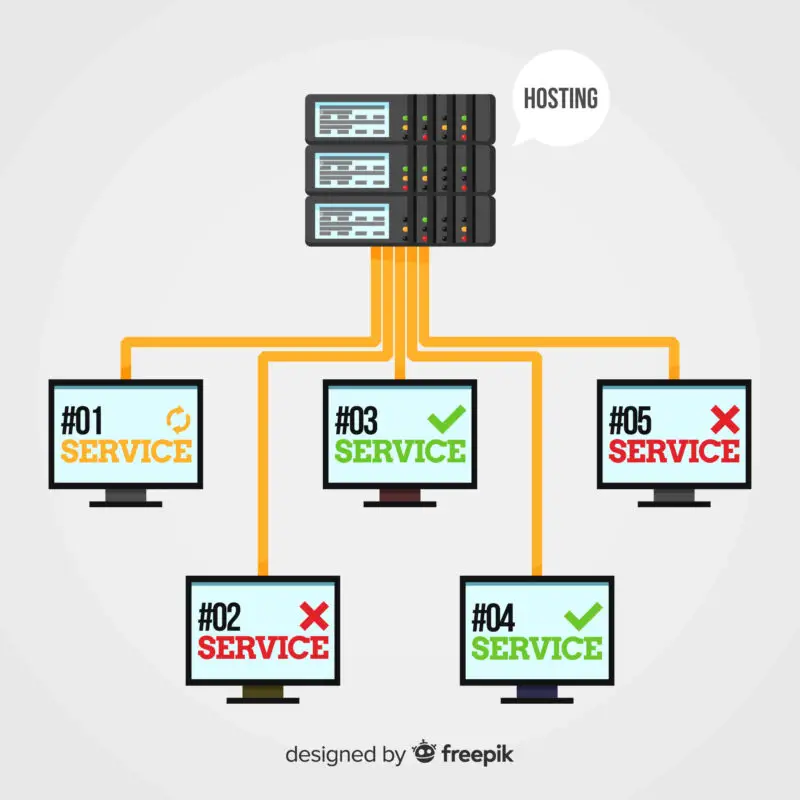
Network topology, refers to the physical or logical layout of a computer network. It defines how devices are interconnected and how data flows within the network. Think of it as the blueprint that outlines the structure and relationships between different components.
What is network architecture?
Network architecture refers to the overall design and structure of a network. It encompasses the various components, protocols, and configurations that are used to create a functional and efficient network system. In other words, it is like the blueprint or master plan for building a network.
One key aspect of network architecture is determining how data will flow within the network. This involves deciding on things like routing strategies, addressing schemes, and traffic management techniques. Another important consideration is selecting the appropriate hardware and software components that will be used in the network.
Security is also a major concern when designing a network architecture. Network architects must ensure that adequate measures are in place to protect against unauthorized access, data breaches, and other potential threats.
Network topology Vs. Network architecture – Key differences
| Network Topology | Network Architecture |
|---|---|
| Refers to the physical or logical arrangement of network devices and connections | Refers to the design and structure of the overall network system |
| Primarily concerned with the layout and connectivity of devices | Primarily concerned with the high-level design and functionality |
| Deals with the arrangement and interconnections of devices within a single network | Encompasses the entire network system, including multiple networks |
| Describes different topological arrangements, such as bus, star, ring, mesh, etc. | Describes the overall design and components, such as client-server, peer-to-peer, etc. |
| Focuses on the flow of data and how devices are physically connected | Focuses on the logical flow of data and the interaction between different network components |
| Considers the physical layout, cabling, and physical connections between devices | Considers the physical and logical components, including protocols, standards, and hardware |
| May not reflect the logical structure or functionality of the network | Considers the logical structure and functionality, including addressing, routing, and protocols |
| May have limitations in terms of scalability as the number of devices increases | Considers scalability factors such as network size, capacity, and growth potential |
| Affects the ease of maintenance and troubleshooting of physical connections | Affects the management, configuration, and overall functionality of the network |
Types of network topologies
There are various types of network topologies, each with its own strengths and limitations. The most common ones include Bus topology, Star topology, Ring topology, Mesh topology, and Tree topology.
Bus topology
In a bus topology, all devices are connected to a single cable called a “bus.” Data is transmitted along this shared medium, allowing for easy communication but also making the entire network dependent on that one central connection.
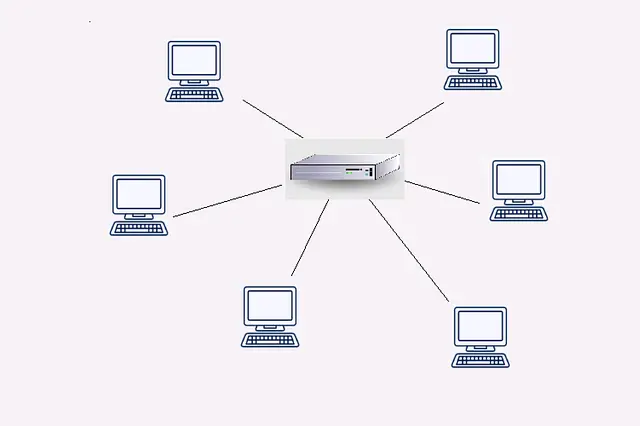
Star topology
Star topology, on the other hand, features a central hub or switch where all devices connect individually. This creates multiple point-to-point connections which can improve performance and allow for better scalability.
Ring topology
Ring topology forms a closed loop where each device is connected to its neighboring devices in sequence. Data travels around the ring until it reaches its destination. This type of setup can be efficient but may suffer from limited fault tolerance if any part of the ring breaks down.
Mesh topology
Mesh topology takes redundancy to another level by providing multiple paths for data transmission between devices. While this offers robustness and fault tolerance, it requires more cables and configuration than other topologies.
Tree topology
Tree (or hierarchical) topology combines elements from both bus and star configurations by organizing devices into groups called segments or LANs (Local Area Networks). These segments then connect through a backbone link forming an organized hierarchy.
Types of network architectures
Client-server model.
In this setup, multiple client devices connect to a central server that provides resources and services. This model is widely used in businesses as it allows for centralized control and management of data.
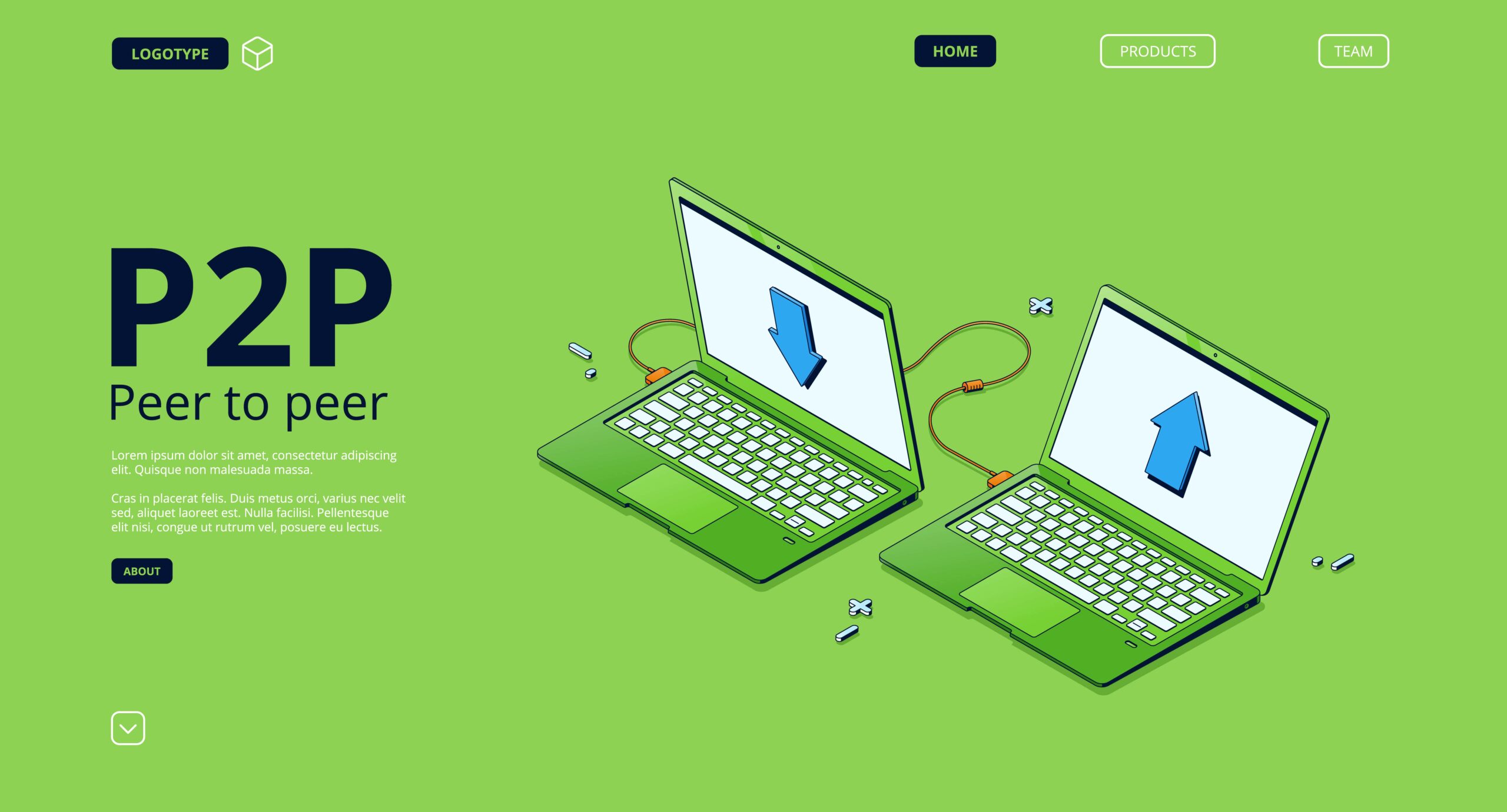
Peer-to-peer (P2P) networking.
Unlike the client-server model, P2P networks do not rely on a central server but instead allow all devices to act as both clients and servers. This decentralized approach can be beneficial for sharing large amounts of data between users.
Cloud-based architectures
Cloud-based architectures have gained significant popularity in recent years. With cloud computing, organizations can store and access data over the internet rather than relying solely on local hardware infrastructure. This provides flexibility, scalability, and cost-effectiveness for businesses.
Virtual private networks (VPNs)
Virtual private networks (VPNs) are another type of network architecture commonly used by organizations with remote employees or branch offices. A VPN extends a private network across a public network such as the internet, allowing secure communication and access to resources.
Software-defined networking (SDN)
Software-defined networking (SDN) is an emerging architecture that separates the control plane from the data plane in networking devices. By centralizing network control through software applications, SDN enables more flexible management and configuration of networks.
Image Credits
Featured Image By – Freepik
Image 1 By – ianlow27 from Pixabay
Image 2 By – upklyak on Freepik