Encryption is the process of converting plaintext into ciphertext, making it unreadable to anyone without the decryption key. Decryption is the process of converting ciphertext back into plaintext, making it readable again with the use of the decryption key.
Encryption
(Image by Pete Linforth from Pixabay )

Encryption is the process of converting plaintext (normal, readable text) into ciphertext (a scrambled, unreadable version) using an encryption algorithm and encryption key. The purpose of encryption is to protect sensitive information by making it unreadable to unauthorized parties, such as hackers or adversaries. Encryption can be used to protect data in transit, such as when sending an email or message, as well as data at rest, such as when storing it on a disk. It can also be used to protect the authenticity of a message, by using digital signature.
What is decryption with example?
Decryption is the process of transforming encrypted data back into its original form. This is done using a key, which is a piece of information that helps scramble and unscramble data. For example, imagine you have a message that you want to keep private. You can encrypt it using a secret key, and then anyone who has that key can decrypt the message and read it.
Decryption
Decryption is the process of converting ciphertext (scrambled, unreadable text) back into plaintext (normal, readable text) using a decryption algorithm and the corresponding decryption key. It is the reverse process of encryption and is used to access the original information that was encoded. Decryption is typically only possible with the use of the appropriate decryption key, which is kept secret and is only shared with authorized parties who are permitted to access the original data. Without the decryption key, the ciphertext will remain unreadable and the information it contains will be inaccessible.
What is difference between decrypt and decode?
Decrypting is the process of taking ciphertext and converting it back into plaintext. Decoding is the process of taking coded messages and converting them back into their original, unencoded form.
How to choose the right encryption method
There are a few different encryption methods that you can choose from, and it is important to select the right one for your needs. For example, if you are looking to protect your data from being intercepted and read by someone else, then you will want to use a stronger encryption method. On the other hand, if you simply need to encrypt your data so that it cannot be easily accessed by unauthorized people, then a weaker encryption method may be sufficient.
Here are some factors to consider when choosing an encryption method:
- The strength of the encryption: How difficult would it be for someone to break the encryption and access your data?
- The level of security required: Are you trying to protect sensitive information or just encrypting data for storage?
- The speed of the encryption/decryption process: Some methods are much faster than others, which can be important if you are working with large amounts of data.
Comparison of popular encryption methods
There are a few different ways to encrypt data, each with its own strengths and weaknesses. The most popular methods are symmetric-key encryption, public-key encryption, and hash functions.
Symmetric-key encryption is the simplest and most common type of encryption. A single key is used to both encrypt and decrypt the data. This key must be kept secret, or else anyone with it will be able to read the encrypted data. One advantage of symmetric-key encryption is that it is fast; one disadvantage is that it requires both parties to share the key beforehand.
Public-key encryption is more complex than symmetric-key encryption, but it has the advantage of not requiring a shared key. Each party has their own private key, which they keep secret, and a public key, which they can share with anyone. Data encrypted with someone’s public key can only be decrypted by that person’s private key. This means that even if someone intercepts an encrypted message, they won’t be able to read it unless they have the recipient’s private key. The main downside of public-key encryption is that it is slower than symmetric-key encryption.
Hash functions are a type of cryptographic algorithm that can be used to encrypt data. They work by taking some input data and outputting a fixed-size “hash” value. Hash functions are one-way algorithms, which means that given some hash value, it is computationally infeasible
Which encryption is safest?
Symmetric-key encryption is the most basic type of encryption, and is also the quickest and easiest to break. It uses a single shared key to encrypt and decrypt data, which means that if the key is compromised, all data encrypted with that key is at risk.
Asymmetric-key encryption is more secure than symmetric-key encryption, because it uses two different keys – one for encrypting data, and one for decrypting it. This means that even if one of the keys is compromised, the other can still be used to keep data safe. However, asymmetric-key encryption is much slower than symmetric-key encryption, so it’s not always practical for large amounts of data.
Hash-based encryption is the most secure type of encryption because it doesn’t use any keys at all. Instead, it generates a unique fingerprint (called a “hash”) for each piece of data. This fingerprint can’t be reverse engineered to reveal the original data, so even if it’s intercepted by someone, they won’t be able to read it. Hash-based encryption is also very quick, making it a good choice for encrypting large amounts of data.
How do I encrypt and decrypt?
As we know encryption is the process of converting plaintext to ciphertext, which is unreadable without a decryption key. Decryption is the process of converting ciphertext back to plaintext using the decryption key.
There are many encryption algorithms available, such as AES, RSA, and Blowfish. The choice of algorithm will depend on the specific use case and the level of security required.
Here is an example of how to encrypt and decrypt a message using the AES algorithm in Python:
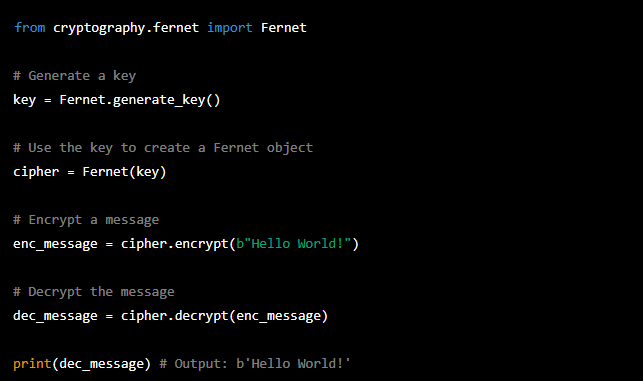
Do hackers use encryption?
Yes, hackers do use encryption to protect their data and communications from being intercepted and read by others. By encrypting their data, they can make it much more difficult for anyone to access and understand it. There are many different types of encryption that hackers can use, so it is important for them to choose an encryption method that is strong enough to protect their data from being decrypted by others.
Can hackers decrypt encrypted data?
In general, hackers cannot decrypt encrypted data unless they have access to the key that was used to encrypt it. However, there are some methods of attack that can be used to try to break encryption, such as brute force attacks or cryptanalysis. These methods can sometimes be successful, but they are usually very time-consuming and require significant computing power.
Frequently asked questions about encryption and decryption
Can you decrypt a password?
Yes, you can decrypt a password, but it depends on how the password was encrypted in the first place. If you know the encryption algorithm that was used, then you can reverse the process to decrypt the password. However, if the password was encrypted with a strong encryption algorithm, then it may be very difficult or even impossible to decrypt it.
Can I decrypt without key?
Yes, you can decrypt without a key, but it will not be readable. The process of decoding without a key is called decryption, and the result is unencrypted data. To decrypt, you need a key that matches the one used to encrypt the data.
Is Whatsapp status encrypted?
Yes, WhatsApp status is encrypted. This means that only the sender and recipient can see the contents of the status update. WhatsApp uses end-to-end encryption to protect status updates. This means that the contents of the status update are scrambled when they’re sent from one person to another.
What is 128 vs 256-bit encryption?
The main difference between the two is the number of bits used to encrypt data. 128-bit encryption uses a shorter key length, which makes it faster but less secure. 256-bit encryption uses a longer key length, which makes it slower but more secure.
How can I decrypt data quickly?
There are a few different ways that you can decrypt data quickly. One way is to use a tool like Data Recovery Pro. This software will allow you to quickly decrypt any type of encrypted data. Another way is to use a tool like DiskDigger. This software will allow you to quickly recover any type of lost or deleted data. Finally, if you have access to the encryption key, you can simply enter it into the appropriate field and click the “decrypt” button.
Does Google use 128-bit encryption?
Google uses 128-bit encryption to protect your information as it is transmitted over the internet. Encryption is a process that transforms readable data into an unreadable format, making it difficult for anyone who does not have the proper decryption key to access the information. 128-bit encryption is one of the most secure types of encryption available, and it is used by many financial institutions and other organizations to protect sensitive information.
Featured Image By – Photo by Markus Spiske on Unsplash








